OpenCTI Install
Installing OpenCTI for Threat Monitoring
Monitoring the world for new and upcoming cybersecurity threats can make all the difference. Knowing the latest threat actor, malware family, target industry and building cohesive timelines can make all the difference with how you or your organization plan for a cyber incident. Most people think this only affects organizations, but it does affect the individuals. We saw this very much with the Ransomware Attack on United Health Care left people stranded with various disruptions to their medical cares and needs.
Change Healthcare Ransomware Attack Having Massive Impact on Providers
UnitedHealth Confirms 190 Million Americans Affected by Hack of Tech Unit
So with this blog, I'm going to walk you through how to monitor for new and upcoming cyber threats using OpenCTI by Filigran.
OpenCTI is a free and open source threat intelligence platform that you can setup in your lab or organization to help expand visibility into threat data. Such as new threat actors, indicators of compromise, malware samples and more. You can set this up in any environment that supports Docker, so regardless of if you're using cloud hosting, dedicated hardware or your own local virtual environment. You can get this platform up and running.
I will be using an Ubuntu Server VM within my Proxmox lab environment but the processes are essentially the same regardless of platform.
So to start, we're going to need to make sure we install Docker Compose. To do this, run the following command.
sudo apt install docker-composeOnce Docker Compose installs, we're going to need to add ourselves to the docker group to manage the docker environment.
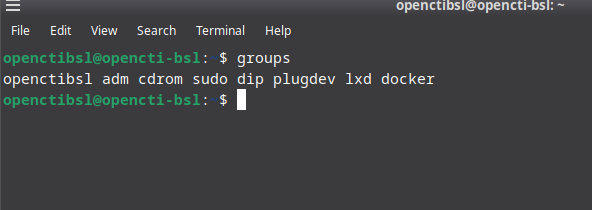
sudo usermod -aG docker $USERSign out of your server, and sign back in and check with the command
groupsYou should now see yourself as part of the Docker group
Next, per OpenCTI's instructions we will want to add the path where we store the docker files so run the following command
sudo mkdir -p /opt/docker && cd /opt/dockerNow we're going to want to go ahead and clone the repository with git clone command.
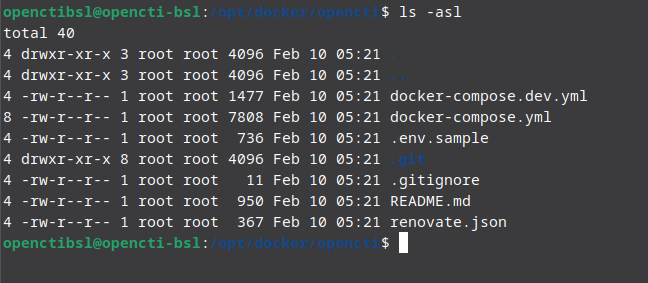
sudo git clone https://github.com/OpenCTI-Platform/docker.git openctiMove the the opencti directory and validate all the files are there. Running an
cd opencti && ls -alwill show us all the files, we need to make sure that we see the .env.sample present in the directory.
Make a copy of that file from .sample to .env with the following command
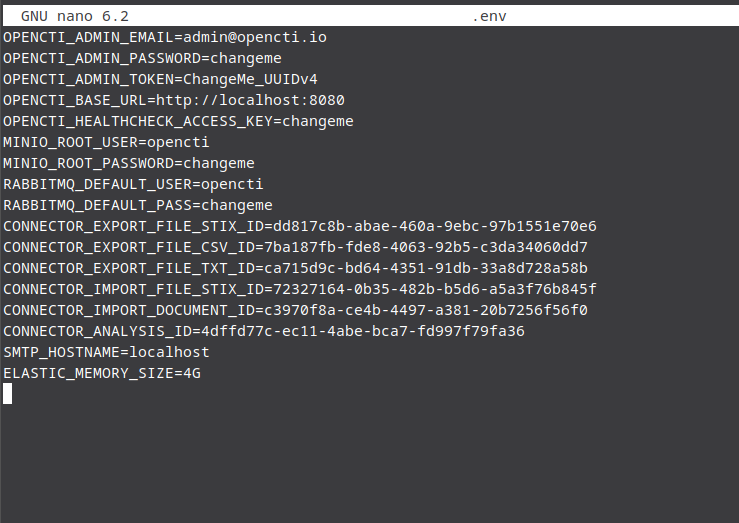
sudo cp .env.sample .envOnce you got it copied over, we need to make some edits to the .env file as by default it looks as such:
There are a few lines we need to modify to make OpenCTI work and is extremely important for adding our connector.
The first, we’re going to want to change our email this is for administrator sign in, so make sure if this is in a production environment, you follow your organizations guidelines, however since this is running in my lab, we are just going to leave it as is.
Next, is the admin password, we are going to also want to make sure this follows best practices especially if this is in a production environment.
Next we will need to generate some UUIDs for OpenCTI, the key one here will be the admin token, as this will point to your OpenCTI Instance for connectors
https://www.uuidgenerator.net/version4
Fill in the rest of the requirements with the UUID’s you need, and fill in the rest of the usernames and passwords again if you’re using this in a production environment be mindful of your organization guidelines also to be sure to include the SMTP Hostname with your email service provider.
(A helpful hint if you're spinning this up within a local self hosted environment, still make the minio and rabbitmq passwords complex, as I ran into this issue trying to spin this up on my own with simple passwords)
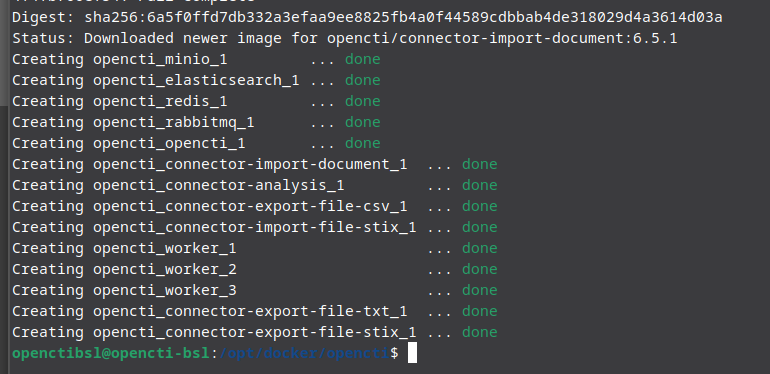
Once that’s completed, go ahead and save it, and run the following commands to build it
docker-compose up -dIf this is your first build, please give it a few minutes as it has to pull all the service containers that opencti relies on so just give it a few minutes.
After everything runs, we’ll want to open a browser and browse to our ip address/hostname on port 8080,
http://<ip_address>:8080where you should be greeted with the login.
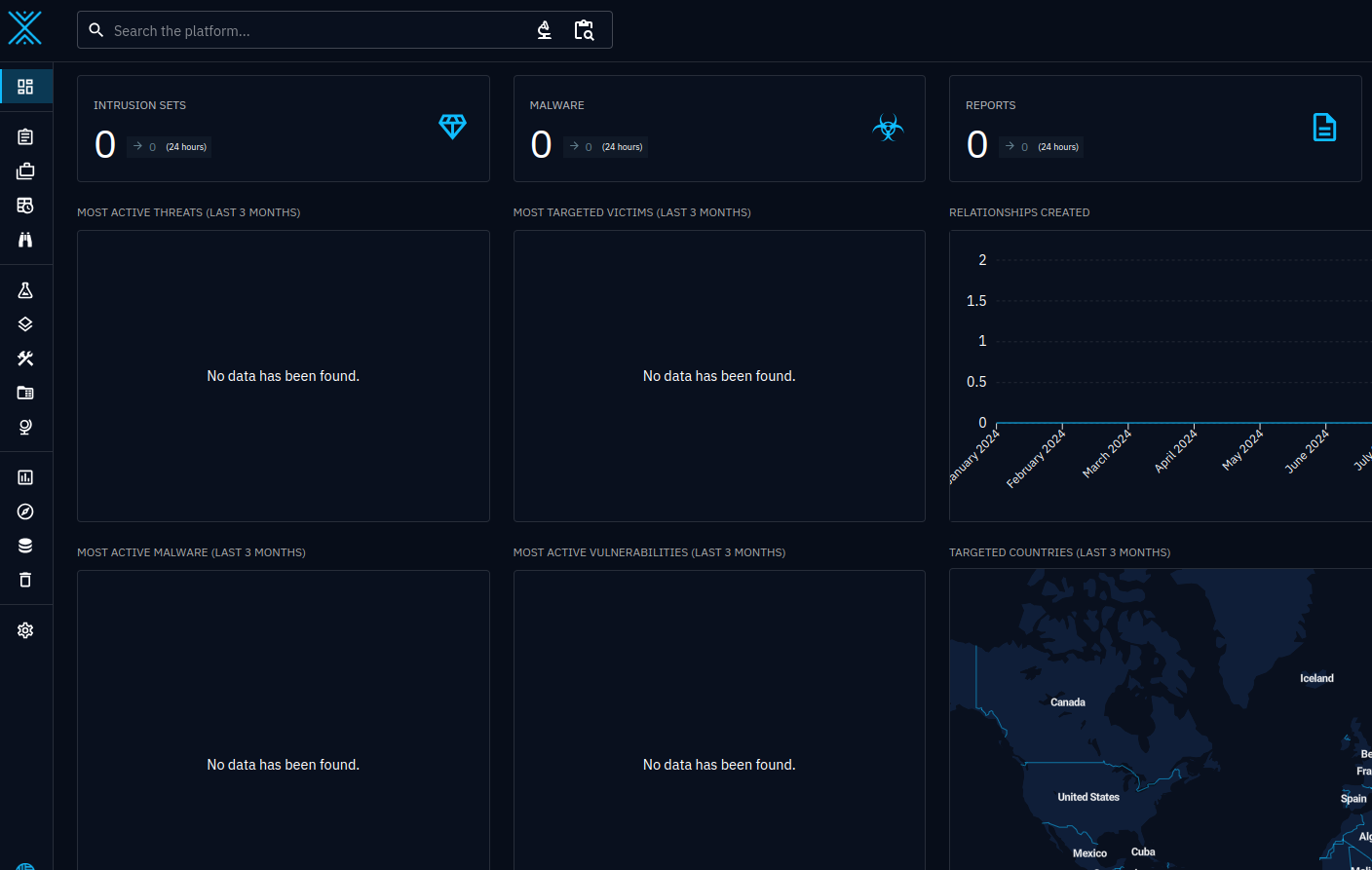
Once logged in, we can see our dashboard is up and running, we can navigate around but we see we have no data. So lets go ahead and add that data in.
One of the most popular connectors to get a good sense of what is happening in the world, is Alien Vaults Open Threat Exchange.
To do this, you will need an account it is free and you can pull a good chunk of data from them and integrate it into your own OpenCTI. Once you sign into Alienvault you can grab your OTX Key from your account. Now we need to head back to OpenCTI's github page and navigate to their connectors.
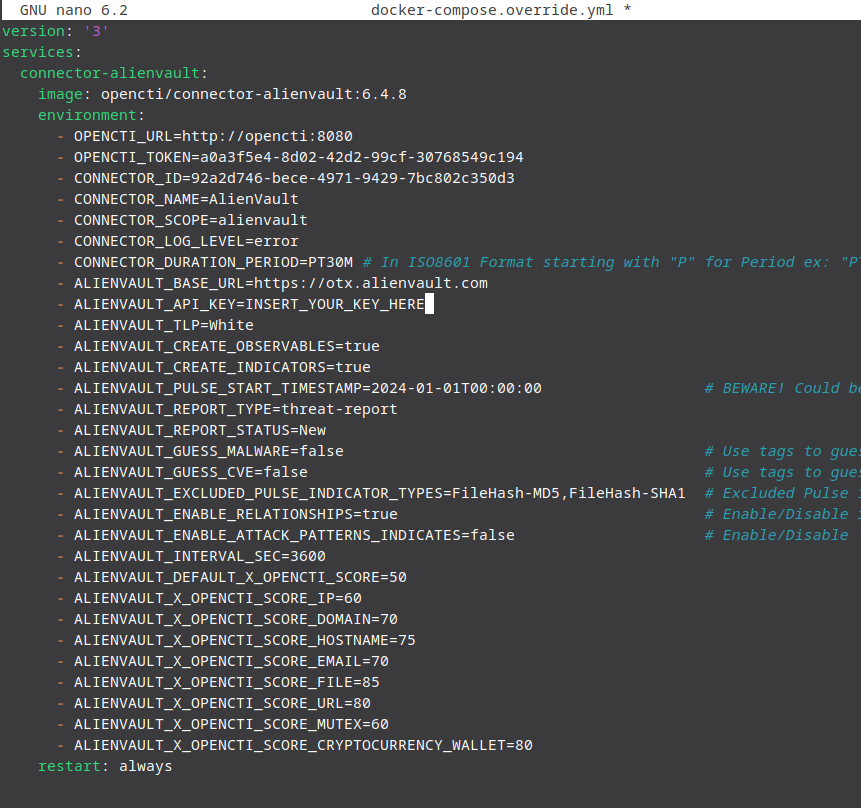
Open up the Alien Vault connector .yml file and copy it. Now heading back over to yoru terminal, you'll want to create an override .yml file with the following command
sudo nano docker-compose.override.ymlThis will allow us to modify our docker environment without modifying the original OpenCTI .yml file.
Paste the copied alien vault connector configuration into this .yml file.
We need to grab a few items. Such as another UUID4 and the connector token from the OpenCTI .env file. Grab those and paste them in their respected fields.
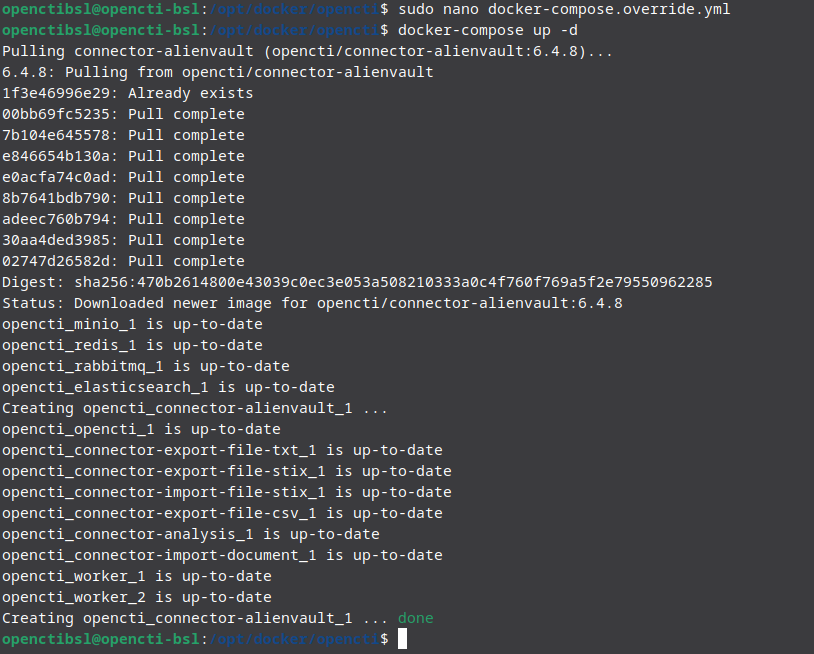
Now with this, depending on your server environment you may want to change the Pulse Start Timestamp, as it dates back to 2022, 3 years ago now. I’ve changed this to make sure I have a smaller more relevant ingestion and moved the year to 2024. Save the docker file and repeat your same processes of spinning up your dockers. You will see that it pulls a new connector alienvault and it’s rather quick to build up
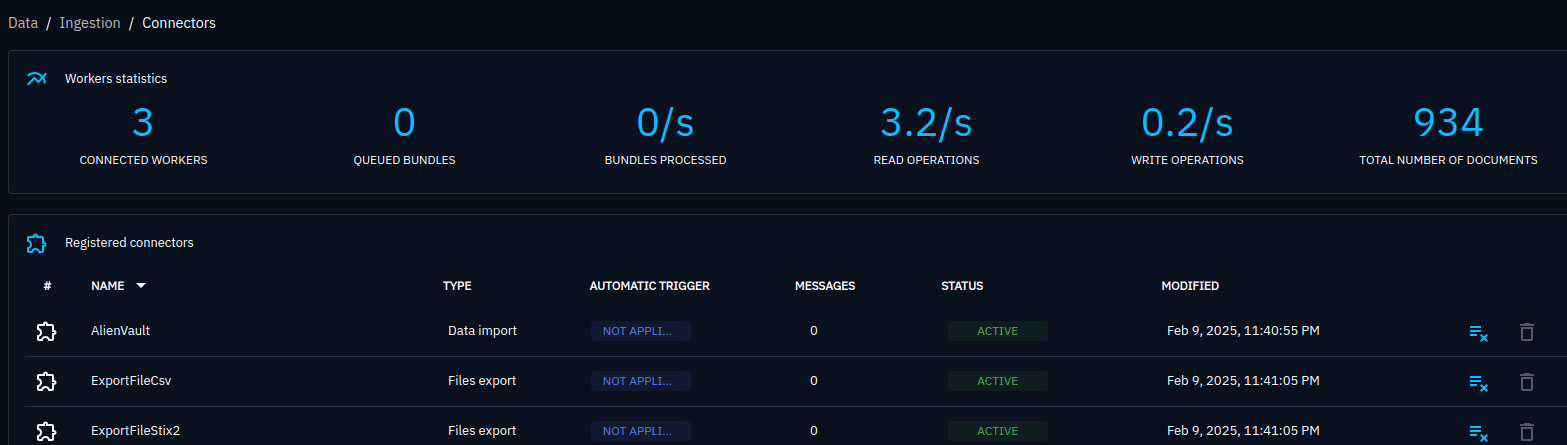
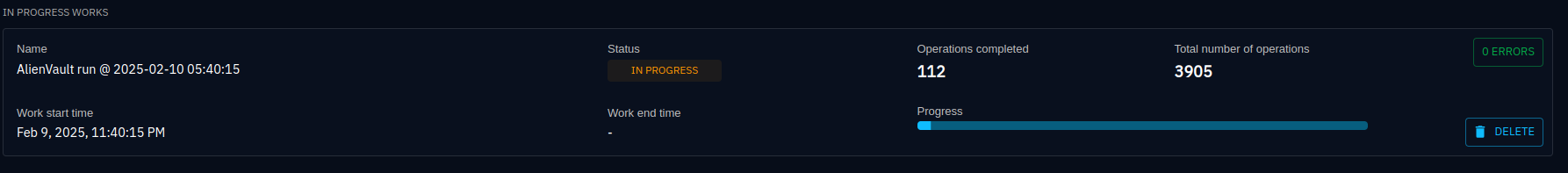
docker-compose up -dNow if we browse to our dashboard and go down to data and to ingestion we will see that Alienvault is there and we will start to see read and write operations with some documents.
Clicking into the Alienvault we can see that the status is in progress. So give this a little bit of time to run.
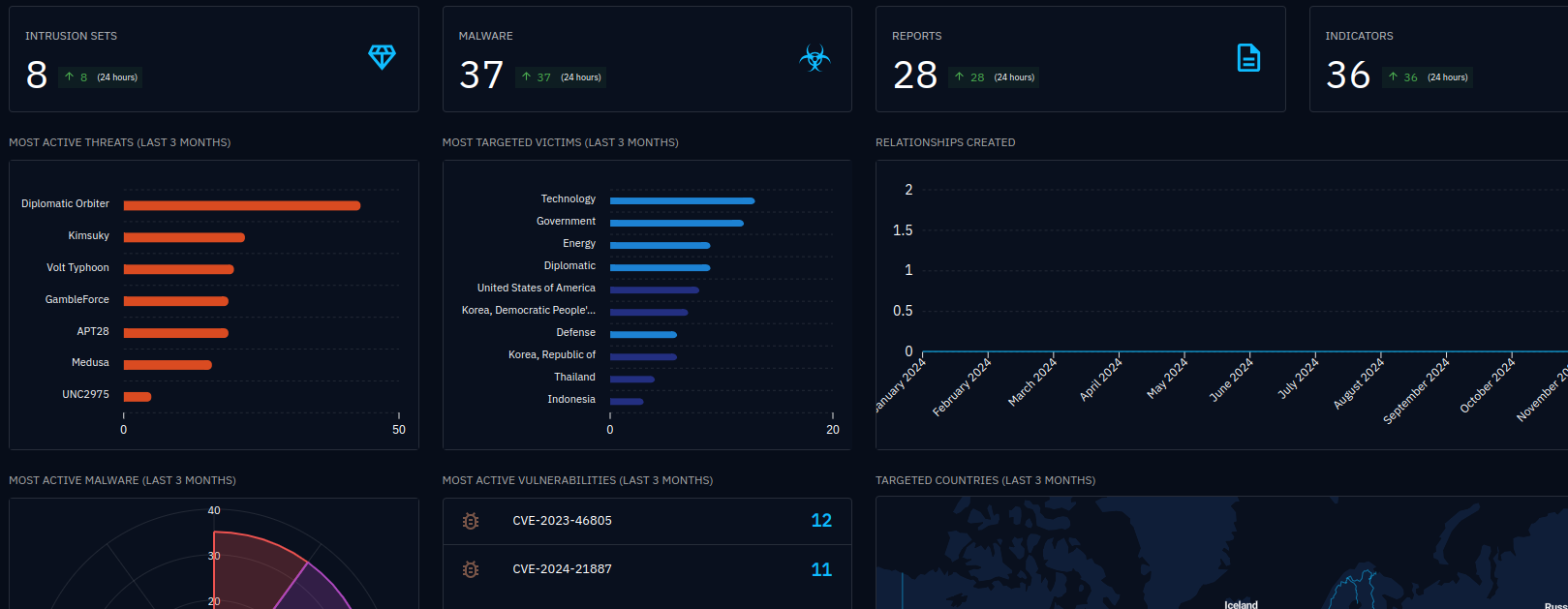
And after a few minutes, if we go back to our dashboard, we see that data is starting to populate into our various preset fields.
To add more connectors, repeat the same process with other connectors in the docker override file and you can ingest more and more data And that’s it! You have your very own threat intelligence dashboard to keep up with new threats that are happening in the world
Happy Threat Hunting!
~Kevin (macros)~